In this post we present the new version of the Burp Suite extension EsPReSSO - Extension for Processing and Recognition of Single Sign-On Protocols. A DTD attacker was implemented on SAML services that was based on the DTD Cheat Sheet by the Chair for Network and Data Security (https://web-in-security.blogspot.de/2016/03/xxe-cheat-sheet.html). In addition, many fixes were added and a new SAML editor was merged. You can find the newest version release here: https://github.com/RUB-NDS/BurpSSOExtension/releases/tag/v3.1
New SAML editor
Before the new release, EsPReSSO had a simple SAML editor where the decoded SAML messages could be modified by the user. We extended the SAML editor so that the user has the possibility to define the encoding of the SAML message and to select their HTTP binding (HTTP-GET or HTTP-POST).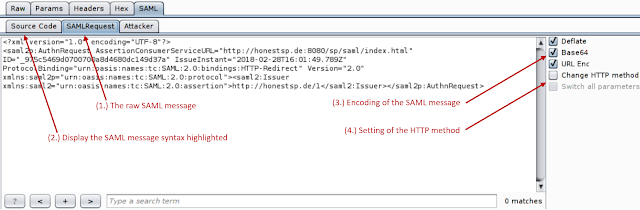 |
| Redesigned SAML Encoder/Decoder |
Enhancement of the SAML attacker
XML Signature Wrapping and XML Signature Faking attacks have already been part of the previous EsPReSSO version. Now the user can also perform DTD attacks! The user can select from 18 different attack vectors and manually refine them all before applying the change to the original message. Additional attack vectors can also be added by extending the XML config file of the DTD attacker.The DTD attacker can also be started in a fully automated mode. This functionality is integrated in the BurpSuite Intruder.
 |
| DTD Attacker for SAML messages |
Supporting further attacks
We implemented a CertificateViewer which extracts and decodes the certificates contained within the SAML tokens. In addition, a user interface for executing SignatureExclusion attack on SAML has been implemented.Additional functions will follow in later versions.
Currently we are working on XML Encryption attacks.This is a combined work from Nurullah Erinola, Nils Engelbertz, David Herring, Juraj Somorovsky, and Vladislav Mladenov.
The research was supported by the European Commission through the FutureTrust project (grant 700542-Future-Trust-H2020-DS-2015-1).
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.